Planning your Instances - Security
IMPORTANT
Change Default Passwords
Consider changing the default password that is set for the user softnas and for root account.
Apply the Latest Software Updates
We identify threats and provide fixes on a regular basis, so be sure to keep up with the latest software updates and maintenance.
Restrict Firewall source IP- Restrict the allowed IP addresses which are allowed access to each port on SoftNAS® - especially HTTPS (port 443).
- Only allow approved administrators to access the SSH, HTTPS ports by restricting who (which TCP/IP addresses) can access those ports.
- Restrict NAS ports (e.g., CIFS, NFS, and iSCSI) to only allow EC2 workload instances; e.g.,x.x.x.x/24 or a specific range of workload instances.
- When publishing storage via NFS, CIFS, iSCSI, or other protocols from SoftNAS® via the Internet, it is also critical to configure encrypted, authenticated access and limit the source ports accordingly.
- Restrict the range of allowed source IP addresses.
- If storage services are published only on an internal LAN or WAN, then apply appropriate security measures as for any storage server in this network environment.
NFS and Bind Services
Buurst's SoftNAS supports both NFSv4 and NFSv3 for legacy purposes. If using NFSv3, a few services may require configuration/definition in order to ensure connectivity through a firewall. Ports will need to be defined and set statically.
NFSv4 only requires port 2049. It may use port 111 for automounting. The other TCP/UDP ports specified here are for SoftNAS deployments using NFSv3.
There may also be some other ports required for clustering, client status, nfs manager, etc. To find out what other ports may need to be available through a firewall you can run the following command from the nfs server:
rpcinfo -p | grep nfs
If you need to define static ports for NFSv3, use a ready-made config file that is configured to use your defined ports. The config file is found at:
/etc/sysconfig/nfs
Create your alternate as:
/etc/sysconfig/nfs.softnas
Then rename it to overwrite the original once the desired ports are defined. NFSv3 will use the ports defined in the config file.
TCP Port | UDP Port | Source | Service |
111 | 111 | x.x.x.x/24 | portmapper |
2010 | 2010 | x.x.x.x/24 | rquotad |
2011 | 2011 | x.x.x.x/24 | nlockmgr |
2013 | 2013 | x.x.x.x/24 | mountd |
2014 | 2014 | x.x.x.x/24 | status |
2049 | 2049 | x.x.x.x/24 | nfs |
CIFS/SMB via Samba
For ease of use, here are the ports to open for two-way CIFS communication with Windows and Linux desktop systems.
TCP Port | Variable | Service |
| 137 | netbios-ns | NETBIOS Name Service |
| 138 | netbios-dgm | NETBIOS Datagram Service |
| 139 | netbios-ssn | NETBIOS Session Service |
| Additional TCP Ports (Service) | Variable | Service |
| 389 | LDAP | Active Directory Mode |
| 445 | microsoft-ds / netbios-ssn | Active Directory |
| 901 | SWAT | Not related to client communication |
iSCSI
TCP Port # | Note |
3260 | iSCSI Target publishing |
ReCaptcha
To prevent brute force password entry into our servers, the SoftNAS login screen uses ReCaptcha. This means that after 5 unsuccessful attempts to log in, Recaptcha will prompt the user to perform an additional action in order to continue attempting new passwords, preventing repeated attempts from eventually guessing the correct login.
Data at Rest Encryption
Buurst's SoftNAS offers encryption for its disks, protecting data at rest. The encryption is FDE (or Full Disk Encryption) and meets AES-256 standards. Encryption is provided at the pool level, using LUKS encryption. To learn more, see Create a Storage Pool.
Enhancement Considerations
The Linux operating system on which SoftNAS® runs includes iptables and the ability to configure firewall rules on Linux to provide an additional layer of inbound and out bound security, should that be desired. For those who are serious about fully securing a SoftNAS® environment, there are numerous sources for best practices on security lockdown of Linux-based systems. Since SoftNAS® runs on a standard Rocky OS Linux-based operating system, the entire spectrum of Linux-based security tools, add-ons and methodologies are available
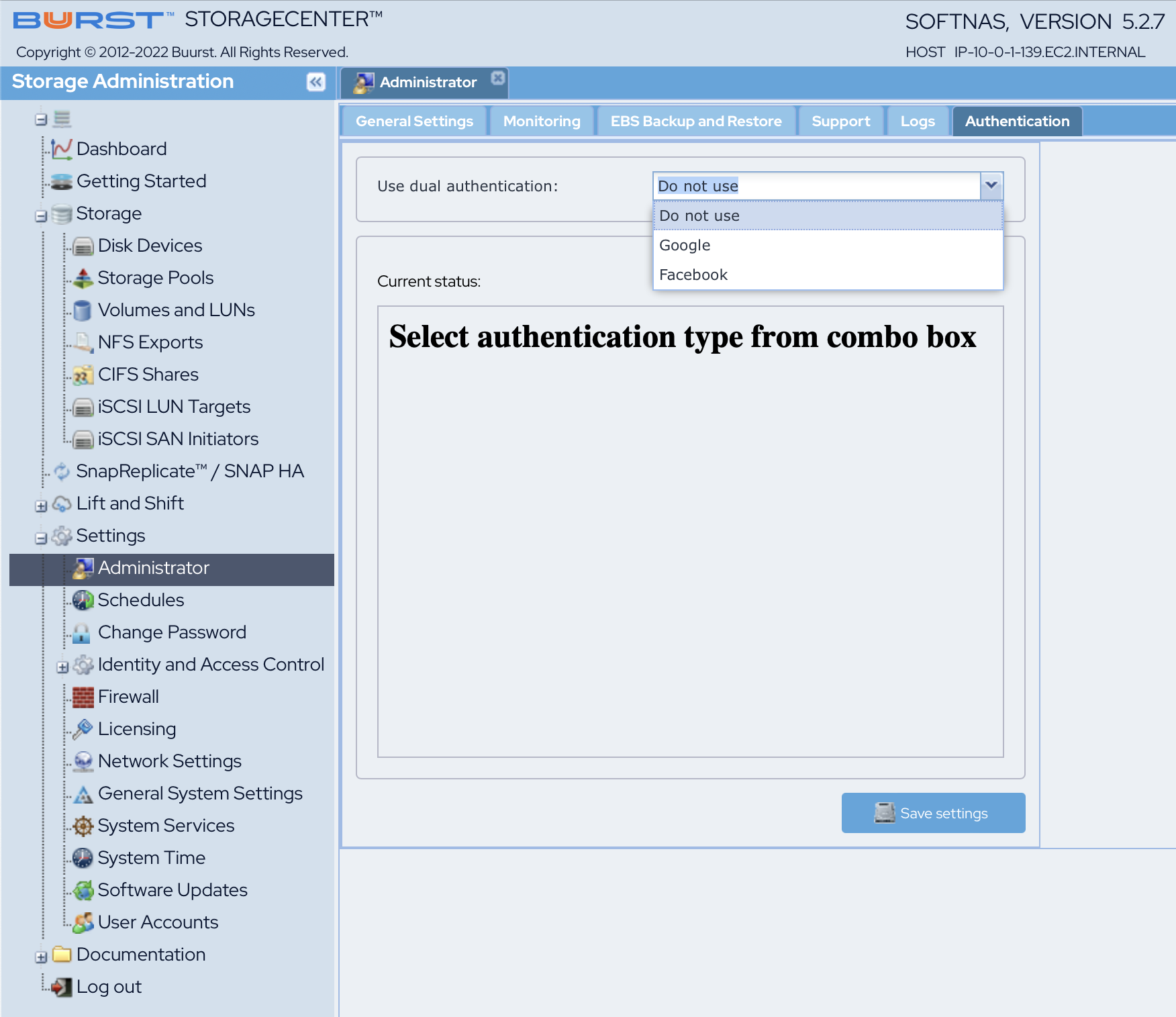
Dual Factor Authentication
SoftNAS supports dual factor authentication through Google and/or Facebook login, in order to add another layer of security to your installation. By requiring not only your SoftNAS credentials to manage your instance, but also login to your Google or Facebook account, your SoftNAS instance is twice as secure. This is an optional configuration, allowing you to select the account you wish to secure SoftNAS with (Google or Facebook) or to opt out.