VORMETRIC TRANSPARENT ENCRYPTION and SoftNAS Filers
VORMETRIC TRANSPARENT ENCRYPTION and SoftNAS Filers
CHALLENGES:
- Customers are interested in Public Cloud storage as a cost-effective solution to on-premise NAS/SAN but weary of the inability to manage Encryption Key. The need is to have the keys outside of the Cloud Providers platform with only the only possibility of un-encryption being a customer regulated action.
- Customers want to be able to have a central repository of the data to manage global access but maintain the ability to silo data for particular regions while keeping the data encrypted to all other locations.
SOLUTIONS:
Vormetric is an agent-based solution that uses the agent along with defined policies to encrypt the data at rest
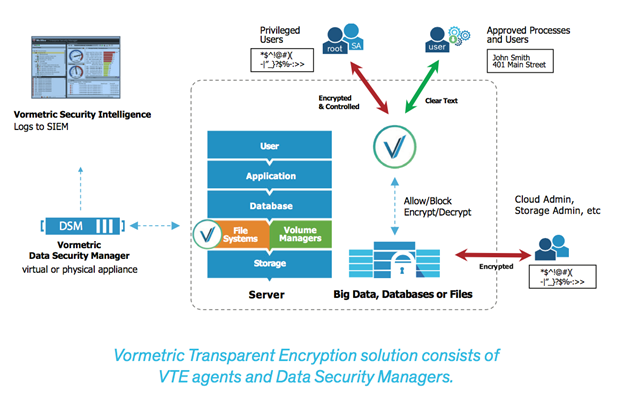
Vormetric Transparent Encryption enables organizations to establish strong controls around sensitive data with maximum efficiency. Vormetric Transparent Encryption delivers data-at-rest encryption for structured databases and unstructured files with centralized key management, privileged user access control, and security intelligence to proactively meet compliance reporting requirements.
The solution can be deployed without any changes to applications, databases or infrastructure so security organizations can implement encryption with minimal disruption, effort, and cost.
Vormetric Transparent Encryption deployments consist of two Vormetric products: Vormetric Transparent Encryption agents and the Vormetric Data Security Manager.
The agents can be deployed across different operating systems across many different environments, however, policy and key management is always centralized with the Data Security Manager
The agent can be installed on multiple platforms at the edge and is responsible for encryption and access:
The agent is available for a broad selection of Windows, Linux, and UNIX platforms, and can be used in physical, virtual, cloud, and big data environments— regardless of the underlying storage technology.
Use of Vormetric Data Security Manager Domains and access to those Domains can be used to silo data especially in scenarios where due to regulations readable cannot exist outside of country or region
Vormetric Transparent Encryption enforces granular, least-privileged user access policies that protect data from APT attacks and misuse by privileged users. Specific policies can be applied by the user (including for administrators with root privileges), process, le type, time of day, and other parameters.
End User always has control of Keys and policy creation through Data Security Manager DSM
All policy and key administration are done through the Vormetric Data Security Manager, which offers APIs and Web-based management interfaces that make policy creation easy.
Vormetric is agnostic as to what type of storage is being encrypted so no configuration or tuning needs to be added to the SoftNAS filer. The share from the filer just needs to be added as a Guarded File System.
- 1. Create a Vormetric Policy
1) Click Policies
2) Click Add Policy
3) Add the following to the policy details section:
Policy Type: Standard
Name: test-transformation
Description: Test Data Transformation
Policy Learn Mode: ☐
Note: The top section, Security Rules, is for the policy access controls and encryption functions. The bottom section allows you to choose which keys will be used in this policy.
4) Click Add in the Security Rules section
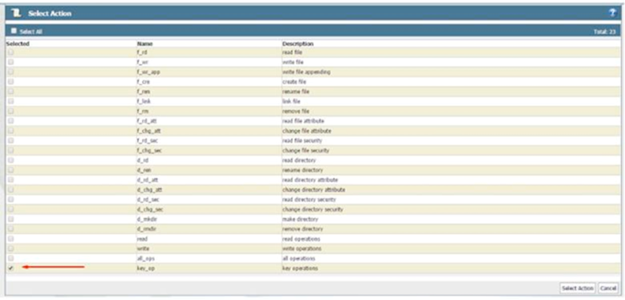
5) Click Select next to the Action field
6) Select key_op at the bottom
7) Click Select Action
8) Click Select next to the Effect field
9) Select Permit and Apply Key
10) Click Select Effect
11) Click OK
Note: By selecting key_op as the action, the DSM recognizes this to be a transformation policy and adds a third “Data Transformation Rules” section. There are now two kinds of policies defined.
Standard Operational Policies
Security Rules - Controls and audits access to the Guardpoint based on a set of criteria
Key Selection Rules - Defines what encryption key will be used when “Apply Key” is selected as an effect
Transformation or Initial Encryption Policies
Security Rules - Controls and audits access to the Guardpoint based on a set of criteria.
Key Selection Rules - Defines what key the data is in before the transformation
Data Transformation Rules - Defines what key the data will be transformed into after the encryption process is complete
12) Click Add in the Security Rules section to add the second rule
13) Click Select next to the Effect field
14) Select Deny and Audit
15) Click Select Effect
16) Click OK
17) Click Add in the Key Selection Rules section
18) Click Select next to the Key field
19) Select clear_key
20) Click Select Key
21) Click OK
22) Click Add in the Data Transformation Rules section
23) Click Select next to the Key field
24) Select NewKey
25) Click Select Key
26) Click OK
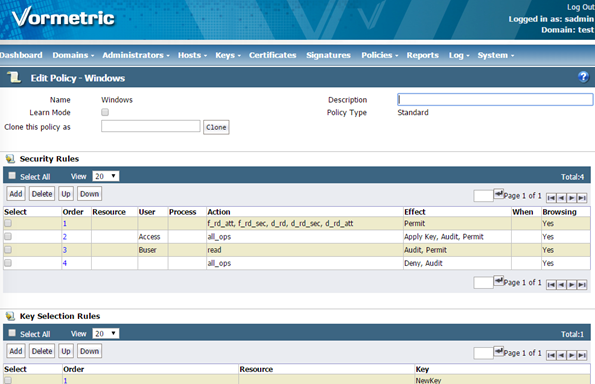
Your policy should look like this:
27) Click OK to save this policy
Note: The effect of this policy is as follows:
Rule 1 – allows the data transform utility to read the data files with clear_key and write the data files with a NewKey key. clear_key represents data not yet encrypted. If the data was already encrypted, then you would use the current key for the data read and the data transform key to be the new key you want the data encrypted width.
Rule 2 – will be applied to all IO activity not handled by rule 1 and deny the IO
- 2. Encrypting the Data
1) Log into DSM Web GUI with access to the Test domain
2) Create a new directory on your Windows system C:\ETEST and a share on your SoftNAS filer \\IP_or_DNS\share\
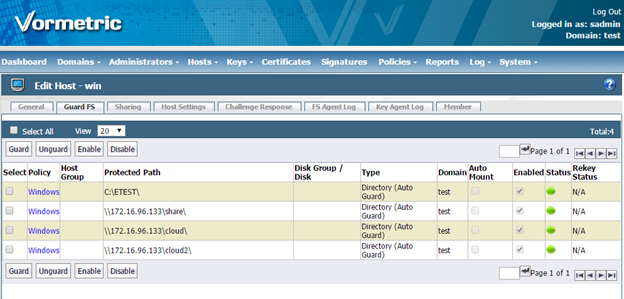
3) Click Hosts
4) Click on the WIN host
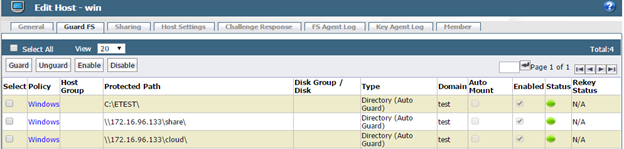
6) Click the Guard FS tab
7) Click Guard
8) In the Policy drop-down menu, select Windows
9) Click Browse
10) From the Remote File Browser, select C:\ETEST and click OK. To guard the SoftNAS share type in UNC entries (\\IP\share or \\DNS_name\share )into the Path field and click OK.
Note: You do not have to use the remote file browser. You can type in entries into the Path field.
11) Click OK to create the new Guardpoint
12) Click Refresh on the page until the status turns green – this may take a few seconds
Note: The Guardpoint is now active and the policy rules are in effect. The Administrator can only perform reads and Access has full access to the data with the application of the encryption key.
13) Switch back to the windows VM RDP session
14) Validate the host has received and implemented the new policy by right-clicking the Vormetric system tray icon and navigating to View>File System>Guardpoints
Note: The files are now encrypted in C:\vipdata2. When Access copies the data to the directory with a Guardpoint applied, the application key is applied because of the “Apply Key” effect of the rule in the policy.
15) Copy all the files within C:\ETEST to C:\ETEST2 to test locally. To test NAS filer Copy all the files within C:\ETEST to UNC path. (\\IP\share or \\DNS_name\share (ex \\172.16.96.133\share\))
16) Open some files in the C:\ETEST2 directory
Note: The application of encryption is completely transparent for Access.
17) Logoff as Access
20) Reopen the RDP session, this time logging in as Buser
21) Open some files in the C:\ETEST2 directory and To test NAS filer open some files in the \\172.16.96.133\share\ or \\172.16.96.133\cloud\ shares.
Note: The behavior of Buser is different than Access. BUser has readability for the files, but without the “Apply Key” effect, the reads are not decrypted.
Conclusions:
Vormetric Transparent Encryption and a SofNAS filer can be used to ensure that customers maintain control of their encryption key locally and can be used on both local and cloud disk to provide encryption at rest.
Vormetric Data Security Manager DSM policies can be used to silo data based on location and even more granular criteria.