Symptoms
On February 16th, a serious defect was found in the getaddrinfo() library call in glibc. This issue, labelled CVE-2015-7547, allows an attacker to cause buffer overflow to occur, creating the possibility of remote code execution in some circumstances. In order to ensure that SoftNAS instances are not vulnerable to this potentially serious security issue, a hotfix has been created in order to eliminate this risk.
Purpose
This KB article provides the steps required to apply the hotfix in order to eliminate the CVE-2015-7547 defect.
Resolution
Log in to your SoftNAS instance using your current credentials.
In the Storage Administration pane, expand Settings, and select General System Settings.
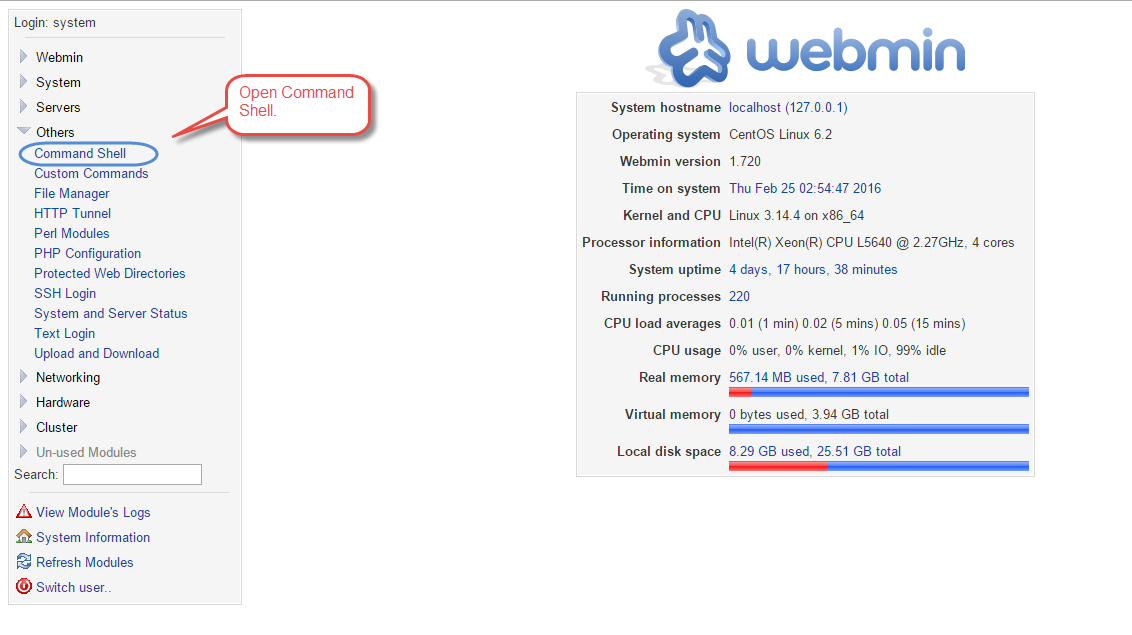
This will bring you to the Webmin Panel. In the Webmin Panel, expand Others, and click Command Shell.
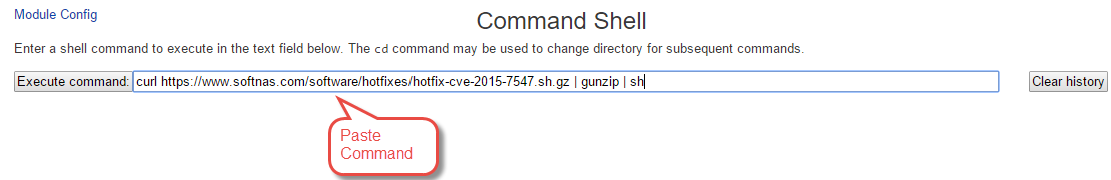
Paste the following command into the Command Shell Applet.
curl https://www.softnas.com/software/hotfixes/hotfix-cve-2015-7547.sh.gz | gunzip | sh
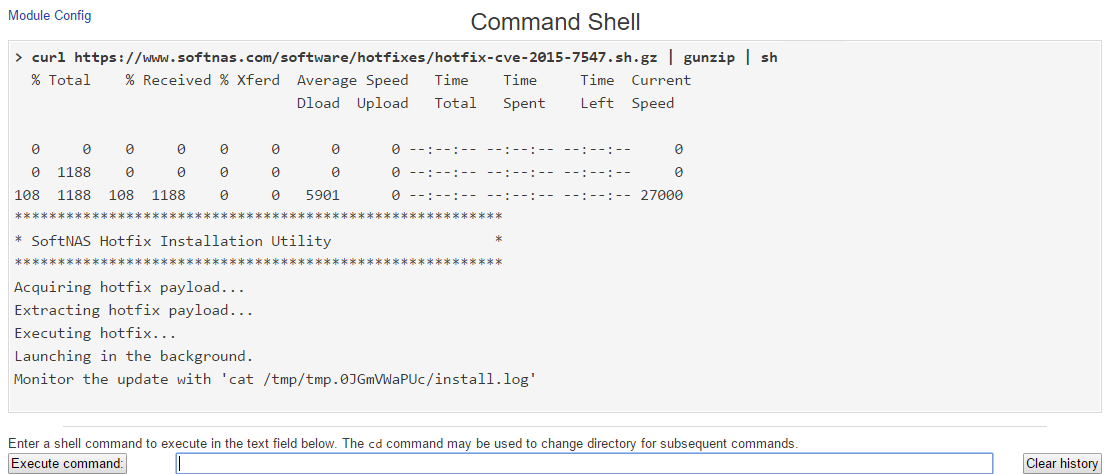
The hotfix will begin installation. To monitor the update, note the location of the install log.